There really is only two ways to configure the Windows Update Agent: Manually through UI or the Windows Update API. Unfortunately as an enterprise admin, you need to use command line utilities to configure endpoints and Microsoft does not provide that. Thus, I’ve put together a really quick command line utility that uses the Windows Update API to allow you to configure using our favorite platform… Tanium.
Download Solution Pack
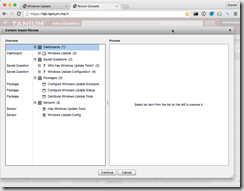
First thing you must do is download the entire Tanium solution pack for Windows Update. Once you’ve downloaded the Windows_Update.xml, you must import it through your Console->Authoring->Import Content.
You’ll find it contains multiple sensors, packages and saved questions for reading and changing the configuration.
Ensure Package Files Download
 One of the packages requires external files that are downloaded from files.danielheth.com. These files are served up via https and thus you must configure my Certificate Authority in order for your Tanium Server to properly download from that location. You must also configure a White Listed URL as well. You can read more about doing this at https://danielheth.com/2015/02/02/secure-downloading-of-package-files-with-tanium/
One of the packages requires external files that are downloaded from files.danielheth.com. These files are served up via https and thus you must configure my Certificate Authority in order for your Tanium Server to properly download from that location. You must also configure a White Listed URL as well. You can read more about doing this at https://danielheth.com/2015/02/02/secure-downloading-of-package-files-with-tanium/
OR you can simply download the three files manually and update the Distribute Windows Update Tools package. We will explore this second option in this article:
Download all following files:
- https://files.danielheth.com/7za.exe
- https://files.danielheth.com/install-wu4tanium.vbs
- https://files.danielheth.com/wu4tanium.zip
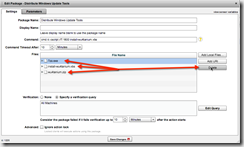
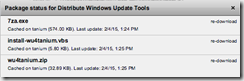
Then edit the Distribute Windows Update Tools package by going to Console->Authoring->Packages, filtering by “Distribute Windows Update Tools” and edit the correct package. Then “Delete” all three files linked to this package…
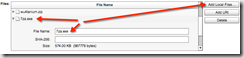
Now we will “Add Local Files…” for each of the three files we downloaded earlier.
Now that we have all three “local” files uploaded into the package we’re ready to start using this solution…
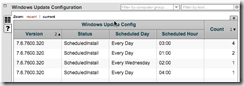
Windows Update Dashboard
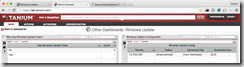
Included in the solution pack is a new dashboard which groups all the functionality together in a single location. Browse to that dashboard by looking under “Other Dashboards” and finding the one called Windows Update.
As you can see from the screenshot, there are two included saved questions. One lets you know about the installation status of the special utility we’re using and the other uses that utility to return the current status of the Windows Update Agent using the API.
Deploy Windows Update Tools
I already have one system deployed with the utility, but my other 9+ systems do not have it. I can drill down to determine what the names of these systems are and distribute to specific machines, but I want my entire infrastructure to have this utility. Thus I will right click on the “No” answer and deploy the package we edited before, the Distribute Windows Update Tools package. Complete the deployment of that action and within 10 or so minutes, you should start seeing the Windows Update Configuration appear in the right answer grid.
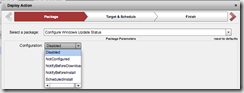
Configure Windows Update Status
The Windows Update Agent has a few modes of operation:
- Not Configured means “not configured” by the user or by a Group Policy administrator. Users are periodically prompted to configure Automatic Updates.
- Disabled is self explanatory… Users are not notified of important updates for the computer.
- Notify Before Download prompts users to approve updates before it downloads or installs the updates.
- Notify Before Installation will download the updates but prompt users to approve the updates before installation.
- Scheduled Installation will automatically install updates according to the schedule that is configured by the user or by the wu4tanium utility.
To make changing this mode-of-operation status easy, I’ve included a Configure Windows Update Status package with the above described options. Select the configuration answers that are not configured as you want and launch this package to change it.
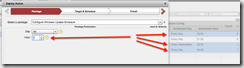
Configure Windows Update Schedule
If you chose to schedule the automatic installation of updates you can use the Configure Windows Update Schedule package to change the day and time updates will install.
I would like all my systems to download and automatically install updates every day at 1am. To do that, select all the configurations that do not match your desires, Right click and Deploy Action. Select the Configure Windows Update Schedule package from the dropdown and two parameters will appear. One to specify the day of the week and the other the hour. The hour is specified in 24-hour “military” time and is only configurable for on-the-hour.
After 10 minutes, the Windows Update Configuration answer grid will start updating with the newly configured schedule. The Windows Update Config sensor is set with a max age of 10min, thus we must wait that long before the sensors script is executed again and the new configuration starts appearing in the answer grid.
Conclusion
I hope this helps those of you who wish to use the Windows Update Agent to update your systems rather than using a more involved patching solution.
Note that this solution DOES NOT USE the Tanium file/shard downloading functionality… each endpoint will download updates directly from Microsoft.
Also I have only tested this on Windows 7 systems. It is possible the Windows Update API will not function as coded on other versions of Windows. If you wish to view the code for the wu4tanium utility, it is available on github. Feel free to fork that project to add functionality or compatibility with other versions of Windows.